Imagine building a big structure like a skyscraper without a blueprint. Inevitably, you’d face endless mistakes, delays, and inconsistencies. Now, apply this analogy to your digital infrastructure, which includes your servers, networks, and databases. For a long time, however, managing these parts felt like building without a clear plan. Engineers would click through screens by hand or write quick scripts. Consequently, this often led to errors and unexpected results.
Fortunately, a better way has emerged: Infrastructure as Code (IaC)/what-is-infrastructure-as-code). This powerful approach treats your infrastructure like software. Specifically, you define everything using special, machine-readable configuration files. This replaces manual steps. Among the many tools for IaC, Terraform stands out. Indeed, IaC with Terraform helps you make even complex cloud systems organized and reliable.
What is Infrastructure as Code with Terraform?
Infrastructure as Code, or IaC, means managing and setting up your computer systems using configuration files. Think of it this way: Rather than plugging in cables or clicking buttons in a web console, you write out your desired infrastructure. This description then serves as the blueprint. Consequently, this description becomes the authoritative guide for your entire system. This approach brings the organized world of software development to managing your infrastructure. You gain benefits like version control, automation, and reusability. In essence, these benefits extend to your digital infrastructure through IaC with Terraform.
Terraform, created by HashiCorp, is a leading tool in the IaC with Terraform domain. It allows you to define what you want your infrastructure to look like. It uses its own simple language, called HashiCorp Configuration Language (HCL). This language is declarative. Being declarative means you describe what you want, not how to achieve it. Thus, Terraform then determines the exact steps to achieve that state.

The Basics of IaC with Terraform
Crucially, this declarative approach is fundamental to IaC with Terraform. It ensures consistency. Your infrastructure will always match the blueprint you’ve written. Furthermore, it allows for repeatability. You can deploy the exact same setup again and again. For instance, this is crucial for consistently developing, testing, and running your applications.
The typical IaC with Terraform workflow involves three main steps:
- `terraform init`: This command prepares your working directory. It downloads required provider plugins.
- `terraform plan`: This command creates a plan. It clearly shows all the changes Terraform will make to your infrastructure. It’s like reviewing a blueprint before construction starts.
- `terraform apply`: This command executes the planned changes. It sets up and manages your resources based on your code.
Overall, this clear workflow for IaC with Terraform removes guesswork. It also prevents unwanted changes. Indeed, this is because you review everything first. Ultimately, it significantly benefits anyone managing modern cloud or on-premises systems.
The Transformative Power: Key Benefits of Terraform IaC
Adopting IaC with Terraform brings many benefits. These can completely change how you manage your digital landscape. These benefits, furthermore, impact every aspect of infrastructure provisioning. This goes from deployment speed to team collaboration. Let’s explore why so many organizations are embracing this powerful approach with IaC with Terraform.
Achieving Consistency and Reliability
One significant problem with traditional infrastructure management is inconsistency. Manual changes or quick fixes, for instance, often create unique setups. These are difficult to troubleshoot if issues arise. Terraform solves this. Specifically, it establishes your configuration files as the authoritative source for your infrastructure.
Consequently, every deployment results in an identical outcome. This helps prevent those frustrating “it works on my machine” problems. Moreover, Terraform is also adept at mitigating “configuration drift.” This drift happens when your actual infrastructure changes. It no longer aligns with your defined setup. Often, this often stems from small, manual alterations. Therefore, by regularly running IaC with Terraform, you can identify and rectify these differences. This keeps your systems exactly as they should be. As a result, overall reliability significantly improves.
Boosting Efficiency Through Automation
Think about the time it takes to manually set up a new server, configure networking, and provision storage. Indeed, when you multiply this across dozens or hundreds of resources, it amounts to significant wasted time. This, in turn, significantly lowers productivity. Fortunately, IaC with Terraform automates these tedious, repetitive tasks. Consequently, this liberates your engineering team. They can then focus on higher-level strategic initiatives and innovation.

The `terraform plan` command is particularly valuable here. Specifically, it gives you a preview of all changes before they are applied. This serves as a crucial safety net. For example, it lets you detect errors or unintended changes before they affect your live systems. This kind of automation with IaC with Terraform significantly expedites deployments. Moreover, it significantly reduces the likelihood of human error. Manual processes, for instance, are prone to such errors.
Embracing Multi-Cloud and Hybrid Environments
Today, many organizations don’t rely solely on one cloud provider. For instance, they might use AWS for some services, Azure for others, and Google Cloud Platform (GCP) for specialized applications. Additionally, some even combine cloud services with their own on-premises data centers. This “multi-cloud” or “hybrid cloud” strategy offers flexibility. But, unfortunately, it can also introduce significant complexity. Thankfully, IaC with Terraform manages this effectively.
Terraform excels in these diverse environments. This is because it is cloud-agnostic. It is not tied to a specific cloud provider. It boasts a vast ecosystem of “providers.” Indeed, these let IaC with Terraform work with almost any infrastructure platform. For example, it includes major cloud providers like AWS, Azure, and GCP, along with VMware, Kubernetes, and many more. This feature ensures a consistent workflow. You can use the same code across all your different platforms. Ultimately, this unified approach simplifies management. It also reduces the need for specialized expertise across disparate cloud tools.
Building with Modularity and Reusability
Just as software developers create functions and libraries to reuse code, IaC with Terraform allows you to build reusable parts of infrastructure called “modules.” In other words, a module is a group of Terraform files. These files are self-contained. Typically, they define a specific piece of infrastructure. For example, you could create a module for a standard web server setup, including its virtual machine, network, and firewall rules.

These modules promote standardization. Specifically, they ensure that everyone on your team uses the same approved configurations. Furthermore, they reduce redundant code. This makes your infrastructure code cleaner and easier to maintain. Most importantly, modules within IaC with Terraform accelerate development. Instead of writing the same configuration from scratch every time, you can simply call an existing module. This allows teams to set up complex systems much faster. And they can do so with increased confidence.
Enhancing Collaboration and Version Control
A core tenet of IaC with Terraform is to treat infrastructure like software. Therefore, this involves storing your infrastructure configurations in version control systems, typically Git. This practice significantly enhances team collaboration. Indeed, every change made to your infrastructure is tracked. It shows who made it, when, and why. Consequently, this creates a clear audit trail of changes.
If something goes wrong, you can easily roll back to a previous, working version of your infrastructure. This offers a safety net. By contrast, manual processes simply cannot provide this level of assurance. Moreover, version control in IaC with Terraform further facilitates team collaboration. For instance, multiple engineers can work on different parts of the infrastructure at the same time. They can use familiar workflows like branching and merging. This shared approach fosters greater team accountability. It also streamlines the entire development and deployment process.
Scaling Your Infrastructure Seamlessly
As your applications grow and user demand increases, your infrastructure must scale accordingly. However, manually provisioning new resources to accommodate increased load can be slow. In fact, it can also lead to errors. IaC with Terraform lets you provision resources on demand. This, crucially, can be done on the fly.
Because your infrastructure is defined in code, scaling it up or down becomes simpler. You just change a few lines in a configuration file and run `terraform apply`. This feature, thus, allows you to quickly and reliably adjust your infrastructure. Therefore, IaC with Terraform is ideal for large-scale deployments. It also effectively manages rapid growth requirements. Whether you need to add ten new servers or hundreds, Terraform can manage it efficiently and consistently.
Navigating the Landscape: Challenges and Considerations for Terraform
While Terraform offers many benefits, it’s also crucial to acknowledge its challenges. After all, no tool is a perfect solution. Understanding these nuances early on will help you optimize your use of IaC with Terraform. Moreover, being aware of these potential pitfalls facilitates better planning and strategy.
Tackling the Learning Curve
For those new to Infrastructure as Code or declarative programming, IaC with Terraform can initially present a steep learning curve. Specifically, it requires dedication to understand its unique declarative language. You also need to learn how to write robust modules and manage the lifecycle of resources. Consequently, it represents a different paradigm than traditional, imperative scripting.
New users, for example, often find it challenging to grasp concepts like providers, resources, data sources, and variables. In addition, they also need to learn how Terraform interprets changes. However, with regular practice and effective resources, this learning becomes more manageable. Investing time in training and practical work with IaC with Terraform proves highly beneficial. The initial effort is significant. But, ultimately, mastering it significantly streamlines infrastructure management.
Mastering State File Management
Terraform uses a “state file” to track the state of your deployed infrastructure. Think of this state file as Terraform’s memory. It records what resources it has created. Furthermore, it also shows how they relate to your configurations. This file is critical. Specifically, Terraform first understands your infrastructure as it currently exists. Then, it compares this to your desired configurations before making any changes.

However, managing this state file can be challenging, particularly in collaborative team environments. For instance, if multiple individuals simultaneously attempt modifications without proper locking mechanisms, it can lead to conflicts. It can even lead to data loss. Therefore, utilizing remote backends (like S3, Azure Blob Storage, or GCP Cloud Storage) with state locking features is a crucial best practice for IaC with Terraform. Proper state management is key. It prevents unexpected behavior. In short, it also ensures infrastructure stability.
Managing Complexity in Large-Scale Deployments
As your infrastructure grows, the complexity of your IaC with Terraform code increases. Indeed, managing numerous environments (like development, staging, production) and thousands of resources can become overwhelming. You might find yourself writing repetitive code for similar resources across different environments. In fact, this repeated code can lead to significant maintenance challenges.
Furthermore, issues in one resource can sometimes propagate to many others unexpectedly. Often, this is due to complex interdependencies between them. Therefore, it’s crucial to implement organizational strategies for your IaC with Terraform code early on. Techniques like using Terraform workspaces, layering your infrastructure (for example, networking in one layer, applications in another), and breaking down large configurations into smaller, logical modules can significantly aid this. Ultimately, good planning and design are key to preventing excessive complexity.
Preventing and Remedying Configuration Drift
While IaC with Terraform aims to prevent configuration drift, it’s not perfect. Nevertheless, drift still occurs when manual changes are introduced to your infrastructure. Indeed, these changes are outside of Terraform’s control. For example, someone might log into a cloud console and manually change a server setting or a firewall rule. This quickly creates a discrepancy between your Terraform code and your infrastructure’s actual state.
When you next run `terraform plan`, it will detect these manual changes. In other words, it will then attempt to revert them. It will set them back to the state defined in your code. This, consequently, can lead to unexpected service disruptions or a reversion to previous configurations if not handled carefully. The best way to combat drift is to establish strict operational policies. Manual changes should be strictly prohibited. Instead, ensure all infrastructure changes are exclusively managed through the IaC with Terraform pipeline. Regularly running `terraform plan` can also serve as an audit. It helps identify and rectify drift before it causes significant issues.
Orchestrating Dependencies and Execution Order
In a complex infrastructure setup, different parts of your system are often interdependent. Thus, for example, a database might need to be created before an application server that connects to it. While IaC with Terraform automatically handles many common dependencies, it can become complex to manage multiple interdependent stacks or modules.
You might encounter challenges if resources require creation in a highly specific order. Indeed, Terraform’s implicit dependency graph might not fully accurately reflect this. Furthermore, mismatched lock files can also cause issues. This is particularly true when switching between different versions of providers or modules. Therefore, sometimes advanced orchestration tools are required to manage the order of numerous separate IaC with Terraform deployments. This ensures that upstream resources are provisioned before downstream components are configured.
Addressing Secret Management Securely
Infrastructure as Code often involves credentials, API keys, database passwords, and other sensitive information. These are known as “secrets.” However, embedding these secrets directly in your Terraform configuration files or version control system poses a significant security risk. Consequently, doing so exposes sensitive data. In fact, this can lead to severe security breaches, even with IaC with Terraform.”
Hence, securely managing secrets within your IaC with Terraform workflows is paramount. Specifically, this involves integrating Terraform with specialized secret management tools. For example, tools like HashiCorp Vault, AWS Secrets Manager, Azure Key Vault, or Google Secret Manager securely store, retrieve, and manage secrets. Thus, by externalizing secrets to these specialized vaults, you can keep your sensitive data out of your codebase. This also ensures it’s accessed only when necessary and by authorized entities. Ultimately, this adds a crucial layer of security to your automated deployments.
IaC with Terraform in the Real World: Adoption, Trends, and the Evolving Ecosystem
Infrastructure as Code is no longer a niche domain for a few experts. Instead, it’s an integral component of modern cloud operations. Its adoption is widespread, with IaC with Terraform leading this transformation. Indeed, understanding its current standing and the ongoing shifts in its ecosystem benefits anyone. This is true for those considering or already utilizing this powerful tool.
Widespread Adoption and Impressive Statistics
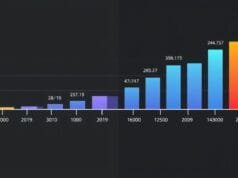
The numbers speak for themselves. A 2023 report revealed that a remarkable 90% of cloud users are now employing Infrastructure as Code. Undoubtedly, this figure underscores the industry’s recognition of IaC’s benefits. These range from enhanced efficiency to stronger security. Moreover, IaC with Terraform has played a pivotal role in its widespread adoption.
Indeed, IaC with Terraform is one of the most popular IaC tools, with thousands of business customers. Specifically, its power derives from its extensive ecosystem. For instance, it includes over 3,000 providers. These providers let IaC with Terraform work with almost any infrastructure platform. Furthermore, a vast library of 12,000 modules offers pre-built, reusable infrastructure components for IaC with Terraform. This extensive collection significantly accelerates development. In addition, it also promotes standardization.
| Statistic | Detail |
|---|---|
| IaC Adoption | 90% of cloud users utilize IaC |
| Terraform Providers | Over 3,000 available |
| Terraform Modules | Over 12,000 in the public registry |
| AWS Provider Downloads 2023 | Doubled from 1 billion to 2 billion |
| GCP Provider Downloads 2023 | Two-thirds of all-time downloads occurred in 2023 |
These numbers demonstrate Terraform’s strong integration with the cloud ecosystem. Moreover, they also highlight its consistent growth. It also highlights its pivotal role in managing modern digital infrastructure. Ultimately, the ability of IaC with Terraform to harmonize diverse cloud environments under a unified workflow is a key reason for its success.
The Impact of Licensing Changes: The Rise of OpenTofu
While Terraform’s popularity is undeniable, it has faced some recent challenges. HashiCorp, the company behind IaC with Terraform, made a significant decision in 2023. They changed Terraform’s open-source license from the Mozilla Public License v2.0 (MPL 2.0) to the Business Source License (BSL). This change, consequently, sparked significant discussion and concern among the developer community.
A survey showed that 56% of respondents called these license changes “disruptive.” Specifically, many worried about the implications for open-source collaboration, commercial applications, and the perceived future of IaC with Terraform. They viewed it as a community-driven project. This change, furthermore, led to a distinct shift within the IaC landscape. As a result, it prompted increased adoption of other open-source IaC tools.
One such alternative that rapidly gained traction is OpenTofu. Indeed, this project started as a direct response to HashiCorp’s license change. It is a community-driven fork of Terraform. Its goal is to keep the tool open-source. The survey data highlights OpenTofu’s rapid growth. Over 40% of respondents reported using OpenTofu. In fact, more than half plan to adopt it in the future. This, therefore, underscores the community’s strong desire for a truly open-source option. This is instead of a commercially-controlled IaC with Terraform.

Furthermore, beyond OpenTofu, other IaC tools are also gaining traction. For instance, these include Pulumi, which leverages common programming languages, and Crossplane, which enables Kubernetes to manage external infrastructure. These changes demonstrate the increasing diversification of the IaC ecosystem. Ultimately, they offer users more choices. These are based on their specific needs and, critically, their preferences regarding open source. Clearly, this period represents a significant turning point for Infrastructure as Code. This includes IaC with Terraform.
The Future Landscape: AI and the Evolution of IaC
The world of technology is constantly evolving, and IaC with Terraform is no exception. Notably, a significant new factor is the growing impact of Artificial Intelligence (AI). AI tools are not just a passing trend. Instead, they are becoming instrumental in accelerating and streamlining IaC adoption and usage. Indeed, they are set to transform how DevOps teams interact with their infrastructure code.
One of the most direct impacts of AI is in creating infrastructure templates. Imagine this: you describe the infrastructure you need in plain language. Then, an AI tool automatically generates the initial Terraform configuration files for you. Consequently, this feature significantly reduces the time spent on boilerplate code for IaC with Terraform. It allows engineers to quickly build new projects without getting caught up in repetitive coding patterns.

Furthermore, AI is proving highly effective at identifying common errors in IaC with Terraform configurations. It can analyze your code to detect misconfigurations, security vulnerabilities, or inefficiencies. Errors such as these, a human eye might miss. This early error detection ensures more robust infrastructure deployments from the outset. Furthermore, it also prevents costly mistakes down the line. Moreover, AI assists in drafting “policy-as-code.” These policies define rules and security boundaries for your infrastructure. They ensure adherence to compliance standards and best practices. AI can assist in writing, validating, and implementing these policies more effectively. This is especially true with IaC with Terraform.
AI Enhancing Infrastructure as Code with Terraform
The true value of AI in IaC with Terraform is not to replace human effort. Instead, it acts as a powerful assistant. It handles the tedious and repetitive tasks. Therefore, this allows DevOps teams to focus on higher-level design considerations. In addition, they can also gain deeper insights into the impact of infrastructure changes. This shift means engineers can dedicate more time to strategic thinking, innovation, and complex problem-solving. Ultimately, AI is poised to make IaC more accessible, robust, and significantly more efficient for everyone involved. It’s a truly exciting time for managing infrastructure.
Your Path Forward with Terraform and IaC
IaC with Terraform represents a fundamental shift in how we manage our digital foundations. In essence, it moves us away from error-prone manual processes. Instead, we move to automated, consistent, and reliable infrastructure. We’ve explored its numerous benefits. For instance, these include consistent deployments, increased efficiency, multi-cloud strategies, and enhanced team collaboration.
However, like any powerful tool, IaC with Terraform comes with its challenges. The learning curve, the intricacies of state file management, and the complexities of large-scale deployments all demand careful consideration and adherence to best practices. We’ve also seen the IaC world evolve. Community-driven alternatives like OpenTofu are gaining prominence. Moreover, AI is set to fundamentally transform how we work with our infrastructure code.
Adopting IaC with Terraform is a prudent decision. Indeed, it offers immense value to any organization committed to modern infrastructure management. Ultimately, it’s an investment in stability, scalability, and security. To begin, start small, grasp the core concepts, and prioritize secure practices, especially for state and secret management. The rewards of a well-implemented IaC with Terraform plan are significant. They lead to faster deployments, fewer errors, and more adaptable infrastructure.
What aspects of Infrastructure as Code with Terraform do you find most appealing for your projects, and what are your biggest concerns about getting started?